Next: Support for Mechanized Theorem
Up: Mobile Registration
Previous: Optional Authentication
At the end of registration, message confidentiality over datagrams sent from
the home agent to the mobile node is implemented through the use of the ESP
header and associated encryption/decryption transforms. IPSEC keys may be
exchanged between a home agent and a mobile node in advance of mobility or may
be negotiated after registration. Such negotiations are outlined in
[8].
Typically, an initially agreed on key should be used only to
encrypt additional keys that are used with the IPSEC headers.
It is standard practice to change data encryption keys regularly.
The addition of ESP to Mobile-IP tunnels is similar to adding ESP
to IP packets except ESP in this case is used in tunnel mode.
In tunnel mode an ESP packet is:
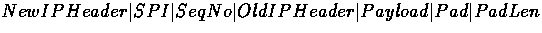

where Payload is a TCP header followed by data.
In our abstract packet format this is:
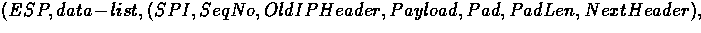
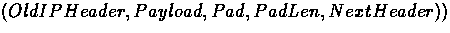
where data-list is the entire packet.
Of course the source IP address for use with the SPI is gotten from the
New IP Header. Again, if the optional authentication is used, then
this header and security mechanism can be shown to provide authentication
and confidentiality over the encryption-data.
This alone only shows that from within a secure enclave, messages can
be sent securely to a mobile node. There are interesting problems
with allowing the home agent to forward messages to the mobile mode from
a source outside of the secure enclave. This allows the possibility of a
chosen plaintext attack since an attacker could observe the encrypted
messages traveling from the home agent to the mobile node.
This is another area for future interesting work.


Next: Support for Mechanized Theorem
Up: Mobile Registration
Previous: Optional Authentication