We want to reduce the problem of testing if the protocol correctly
authenticates the two users to a problem of information flow control between
two levels. For this reason the process actions have been divided into
high and low level actions (sets ![]() and
and ![]() ). Since we want
to check the influence that an intruder can have on the protocol execution,
). Since we want
to check the influence that an intruder can have on the protocol execution,
![]() is composed by the action fake, which is executed at every
Enemy iteration and so can be seen as an abstraction of the Enemy
activity. All the other actions belong to the low level.
is composed by the action fake, which is executed at every
Enemy iteration and so can be seen as an abstraction of the Enemy
activity. All the other actions belong to the low level.
![]()
where:
Since we want to focus on the ``correct'' execution of the protocol, we
consider, for the analysis, only the actions representing the start and the
correct termination of a session between ![]() and
and ![]() :
:
![]()
All the other actions are hidden. So, we define process Protocol' as follows:
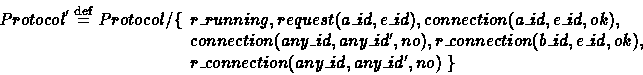
The security property we automatically check is SNNI, which is equal to NDC. The tool used for this analysis is the Compositional Security Checker (CoSeC), a semantic-based tool for the automatic verification of some compositional information flow properties [FG96,FG].
In particular, using CoSeC, we check if the following holds:
![]()
As we said above, the action fake represents the Enemy activity.
So we can
see ![]() as the protocol on a completely secure
channel (i.e., with no enemies), and Protocol'/fake as the protocol under
the Enemy attack. If these two processes are not equivalent we can conclude
that the Enemy is able to interfere with the correct execution of the
protocol.
as the protocol on a completely secure
channel (i.e., with no enemies), and Protocol'/fake as the protocol under
the Enemy attack. If these two processes are not equivalent we can conclude
that the Enemy is able to interfere with the correct execution of the
protocol.
The automatic check gives the following answer:
falsewhere action
Agent Protocol'/fake
can perform action sequence 'r_connection_b_a_ok
which agent Protocol'fake
cannot
![]()
This means that user B is convinced to have established a connection with user A , while A has made a request to user E : hence, the enemy has cheated B .
To realize the cheat, two runs have to be active at the same time: one
between the users A and E , and one between the users E (the intruder
that claims to be A ) and B . Using ![]() and
and ![]() to indicate the
two runs, the sequence that allows to cheat is:
to indicate the
two runs, the sequence that allows to cheat is:
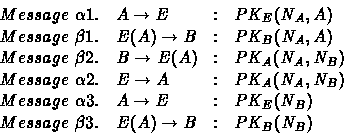
In message ![]() , A sends his nonce and identifier to E , trying to
establish a connection with him. When E receives this message, (s)he
forwards it
to B , pretending to be A (
, A sends his nonce and identifier to E , trying to
establish a connection with him. When E receives this message, (s)he
forwards it
to B , pretending to be A (![]() ). B accepts the
message and sends back his nonce and the nonce just received (
). B accepts the
message and sends back his nonce and the nonce just received (![]() ). E
intercepts this message and, since he cannot decrypt it, he uses A as an
oracle forwarding to him the massage (
). E
intercepts this message and, since he cannot decrypt it, he uses A as an
oracle forwarding to him the massage (![]() ). A accepts and decrypts it;
then he sends to E the last message containing
). A accepts and decrypts it;
then he sends to E the last message containing ![]() (
(![]() ),
considering established the session with E . In this way E has learn
B 's nonce: then he can send it back to B (
),
considering established the session with E . In this way E has learn
B 's nonce: then he can send it back to B (![]() ), that thinks to
have just established a session with A .
), that thinks to
have just established a session with A .
The problem is in message 2 of the protocol that contains the two nonces. Since there is no identifier in it, anyone can intercepts and forwards it claiming to be anyone else.
The correct version of the protocol is:
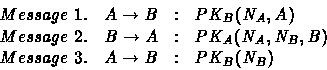
Where message 2 now contains also the sender identifier.
Using again SC to analyze the corrected formalization, we can see that now the agent Protocol' satisfies the SNNI property, so we can conclude that Enemy is not able to interfere with the protocol.
The formalization used so far presents some limitations. For example, only one session can be established. In [Ghe97] it has been studied an improved model which allows the execution of multiple sessions. Another possible extension of the model is related to the equivalence notion used in the analysis. Trace equivalence is not able to detect deadlocks. In [Ghe97] this protocol has been analyzed also with respect to a stronger equivalence notion (bisimulation equivalence) which is able to detect the presence of deadlocks.